Post by frostysh on Nov 16, 2014 11:47:00 GMT 2
Tor net with HTTPS
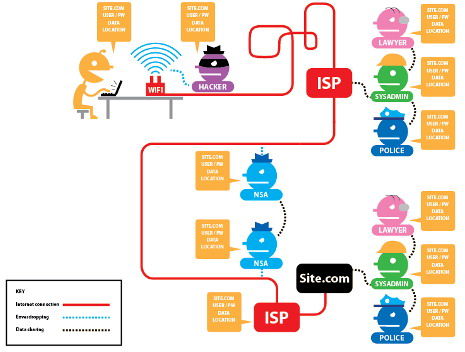
Tor net, деяка дивна зона у свтовій мережі, яка ще називається даркнетом, в основному її використовують хакери і торговці забороненим товаром, цю зону активно контролюють спец. агенства.
У ній досить важко відслідкувати користувача.
Для гравців вона може бути корисною якшо тебе незаконно забанили на якомусь серві, головне пам'ятати про те що у Тор зоні потрібно дотримуватись правил перестороги і НЕ ЛІЗТИ ТУДИ: КУДИ ЛІЗТИ НЕ ТРЕБА... Ну якшо ви звичайно не Про-хакер.
Нижче приведу корисні поради по безпеці.
автор In Pain
Here's my small discussion regarding security and some of my personal recommendations/advice. A lot of it's quite basic or logical and/or already covered by other users, but it's important to take security seriously and better to repeat, than risk new users missing important suggestions. I highly recommend reading the replies. Other members have contributed with various useful information.
If you think I have missed some important point, you disagree with me regarding something or I have made some mistake, then please reply and help everyone to stay safe!
Open source isn't silver bullet regarding security
There's reasonable risk that some component in Tor Bundle (for example Firefox which Tor Browser is based on) containing a security vulnerability: either at the moment or in the future.
First of all, mistakes are made by even most careful and professional software developers from time to time. Also, from time to time they aren't discovered for a long time. This includes security sensitive applications.
Good example was buffer overflow exploit in FreeBSD's telnetd daemon (CVE-2011-4862). The exploit made attacker possible to gain full access over affected system without any authentication. It's good example for several reasons: source of FreeBSD's telnetd daemon is freely available, it's security sensitive application (providing remote access), the bug isn't especially unique in C-code or hard to discover AND the faulty code was almost 20 years old before the vulnerability was (publicly) discovered! It may have been discovered by black hats a long before that though. Of course, one reason why the bug may had persisted so long may have been the decrease in telnet use: since year 2001 it was disabled by default in FreeBSD. Still, it's pretty mind-blowing how the faulty code wasn't already discovered by developers long before that.
Who doesn't know, then telnet is protocol that was created to provide remote access to devices (mostly servers). Nowadays, of course, SSH is recommended in almost all cases over telnet, because it's more secure already by the design.
Such security vulnerability may also be carefully planted there by government agencies. Being open source doesn't magically protect against it. An agents may pose as developers and "help" with the development. They may commit several useful and innocent updates firsts. Then, at some point, they may introduce several changes that seemingly fix or upgrade something. However, together those changes also create some security vulnerability. It's not like they would just commit patch that is obviously malicious, but something that is sneaky and inspecting those changes separately may not reveal the "bug". Even by reading whole code may not help unless the person is very competent in security, cryptography, networking, interaction between different system components and so on.
One leaked NSA presentation ('Tor: Overview of Existing Techniques') even mentions influencing the future development of Tor. Who doesn't know, then an interesting side-note: Tor was initially sponsored by the U.S. Naval Research Laboratory.
The increased security of open source comes from the fact that it's possible to inspect the source code, however average Joe isn't able to understand single line of Tor's code. Even most of experienced developers aren't likely very knowledged in advanced cryptography. So, actually there are limited people who have competence to peer review Tor project.
Of course, Tor is developed and monitored by security professionals, but they are also humans and prone to make mistakes or may miss planted vulnerabilities.
I think, it's reasonable to believe that because Windows is most widely used, then its Bundle is also main target for "malicious forces". However, budget of NSA is big enough to also search them or plant vulnerabilities to Linux and/or its Tor Bundle.
I'm not somehow saying that open source is less secure than closed source projects: of course, the more eyes on the code, the better. I advocate use of Linux and other open source software. However, I think it's important that people don't have false sense of invulnerability!
Whonix
There's interesting project called Whonix (Anonymous Operating System).
Clearnet:https://www.whonix.org
It consists of two virtual machines. One is gateway, on which Tor runs and another workstation, that can only connect to the former virtual machine and is otherwise isolated from network. While using Whonix's workstation all your connections go through Tor. That structure is superior to Tails, because even if Whonix's workstation gets completely infected (for example by exploit in browser), it cannot leak your real IP-address (even if malicious software has gained root user privileges). At least without "breaking out" of the VM somehow: virtual machine software may also have vulnerability, but creating such specific malware is unlikely scenario, because I think they'll try to attack as wide audience as possible.
When using Whonix, then I wouldn't save the state of workstation before closing it, rather always return to the initial snapshot. In such way, when booting it up next time, there will be no traces of previous usage in VM.
Of course, it's important on where you run Whonix virtual machines. It would be wise to have special computer with encrypted hard-drive for that. I would also choose Linux as host for that computer for obvious reasons.
At least at the moment I'm not going write a guide for using Whonix. You should find enough information from their wiki and if that's overwhelming task for you, then better go with Tails. Otherwise, it's high possibility that you do something wrong and end up with less secure system, than even just using Tor Bundle on your current OS.
All my previous text about either accidental or planted security holes also apply on Whonix. Also, setting up such system is certainly somewhat harder than using Tails, but something to consider if you feel like need extra security: e.g. being large vendor.
Tails
Clearnet:https://tails.boum.org
For most users, I recommend Tails. It's still good idea to have a separate computer (cheap netbook for example) on which you run Tails. To be even more safe, use different public or cracked WiFi spots (not the same one, 100m from your apartment). If you go that way, then don't ever even turn on your netbook when you're at home. However, those are just extra precautions you may or may not take: depending how secure you want to be and how heavy is your relationship with darknet (high profile vendor vs small-time buyer).
If information from Tails official web is not enough for you get it up and running, then we have step-by-step guide here in forums:
TAILS in 9 easy steps! by SuperMario
If you have any questions, then feel free to post them here or to SuperMario's thread. I'm sure we can help you out and it's always better to ask, than risk doing something wrong, when security is concerned!
It's also possibility to run it in a virtual machine (such as VirtualBox - clearnet:https://www.virtualbox.org ), but I consider it reasonable only if your host system seems secure. In my opinion it would require full disk encryption and Unix-based OS to start with. However, if you want set up something like that then I think you should consider Whonix instead, because it's meant to run in virtual machines. Tails is meant to be booted from and running it instead in your everyday Windows host may give you false sense of security. I consider it better than running just Windows Tor Bundle, but you can do better and be more safe.
Encryption
Encryption, encryption and more encryption! I think the importance of encryption has been emphasized a lot by different users already, but I still go over it once more.
Encrypting communication
PGP encrypt your messages. My suggestion is gnupg based utility named gpg4usb ( clearnet:http://gpg4usb.org ). It's easy to use, fast, portable and seems to be frequently updated along with new releases of gnupg. It works on both Windows and Linux, which also means that you don't have to export and import all keys to some other software, when you decide to change operating system. I suggest to keep it inside TrueCrypt volume.
There's again a step-by-step gpg4usb guide available in our forums:
EASY TOR & PGP 4096 RSA (Step by Step Guide) by MachineElves
If you have any questions, then feel free to post them here or to MachineElves's thread. I'm sure we can help you out and it's always better to ask, than risk doing something wrong, when security is concerned!
Keys should be at least 2048 bits long, but I recommend using 4096 bits. There's no reason to use shorter key as nowadays' computers are fast enough to use 4096 bits long keys without noticeable delay. Some experts think that for example NSA has enough computing power to break shorts keys (1024-bits) or at least will have in near future. That's more than feasible. Larger key size means exponential, not linear, increase in computer power to use (or break it). That means using too long keys (more than 4096 bits) is overkill: they require more computer power to use, are incompatible with some software, but I think that in foreseeable future, breaking them would be possible only with quantum computers, but that renders whole RSA algorithm useless anyway. There aren't any practically usable quantum computers yet, unless they were developed in complete secrecy, but I find it unrealistic, that they have been able to accomplish that yet.
I recommend encrypting all your private messages with vendors: no point risking leaking any information. Encrypting your address should be an unbreakable rule! Never, ever deal with a vendor, who doesn't use encryption. Period. If he's not able to do that, then how can you trust him with your information anyway.
Encrypting data
For encrypting data I personally recommend TrueCrypt ( clearnet:http://www.truecrypt.org ) and dm-crypt. Latter is for encrypting Linux systems: Ubuntu has made it very easy to select it during the install. My suggestion is to encrypt everything on your computer and also create hidden TrueCrypt containers for especially sensitive information, that you may want to also backup. I'm aware of issues regarding TrueCrypt (license and being closed source), but still think that currently it's feasible option without good enough alternative. If you're Windows user, then I suggest full-disk encryption with it. In my option full system encryption is a must for whatever OS you are using.
Even if you're using Tails as suggested, then are you sure, that your main system doesn't contain any somewhat sensitive information (including caches etc.)? I doesn't mean that Tails leaks anything, but your regular computer usage. You never know what may used against you. In the same idea in mind, to increase overall security, I suggest moving to a Linux. Ubuntu is really easy to use, large package collection and large community to help you out in case of problems.
If you suspect that your computer is about to be confiscated (e.g. hear your door kicked open by screaming men), try to cut the power (or at least lock account/log off). I'm not sure whether it's used in the wild, but it's possible to (literally) freeze computer's RAM and retrieve encryption key(s) from there later.
For encryption use secure password and don't store it (besides your memory) or reuse elsewhere.
I recommend it being at least 20-35 characters. There are different techniques to create secure and memorable passwords. For example: go for password length and combine yourself some long, but memorable sentence to use as password: throw in some numbers, some word(s) that aren't in dictionary, intentionally misspell words, mix words from different languages, using spaces is good if allowed, play with case of letters, same goes for non-ASCII symbols, use regular ASCII symbols (change some letters or words for symbols or numbers: at -> @, i -> 1) and numbers in sentence so it makes sense for you (crak1ngMyPwdIsEasyIfUHave100YEARS@YourArze,NSA! should be pretty okey). Warning! System encryption password is asked during boot and depending on software and/or configuration you may have different keyboard layout then.
Think about your password as your theoretical adversary: 1) can he somehow guess it by knowing your information (e.g. your favorite quotes from facebook) 2) how realistic is that system with a lot of computing power is able to crack it in realistic time (either by combining words from dictionaries or by brute-force).
Because, losing the password means losing everything you didn't have backed up, you may want to temporary save it to some USB-stick encrypted by some easier password that you have already memorized. Then when you have used the password for a few weeks and are sure that it has been saved to your long-term memory, then securely delete the file from USB-stick.
Securely deleting files
Remember that deleting files from disk doesn't actually remove the data. It only marks those sectors as available for new data and old content of those files will be over-written, when those sectors are needed by new data. There are many free tools to securely remove files or to overwrite data of previously deleted files (free space) - that means over-writing those sectors with random information. For Windows one such tool is Eraser ( clearnet:http://eraser.heidi.ie ), for Linux shred. Shred is a part of GNU Core Utilities and thus likely already available to you: just 'man shred' for instructions. It's possible to over-write files by multiple passes: if over-written once then special forensic tools (hardware based) may still be able recover information.
Full disk encryption help avoiding need to shred files, but I still suggest to over-write most sensitive information. As I already noted under encryption, there are at least theoretical ways to retrieve encryption key(s) from powered on machine even if it's locked and you may not have time to even lock your account. Also, you may have to give up your password for some reason or the password may be leaked/cracked.
Common sense
Use your common sense!
Don't re-use your password (and maybe username if you aren't vendor) at different marketplaces. Also use different password for forums as it usually is separate from main site and runs public software. It's harder to protect Tor sites against attacks than clearnet ones: consider that when choosing password.
Think about what information you're sharing! Both dark- and clearnet. We are talking about how important is to use Tails and etc., but remember DPR's fall. As you can read from his arrest warrant, it wasn't technology, but human error(s), that lead to his and subsequently SR1 fall. Never use same username(s) in clearnet. Sharing your referral link? I suggest you don't post it on your facebook wall. Remember that most sites (for example facebook, stackexchange) store ALL your data FOREVER: that includes changes, deleted content and so on. Also, search engines crawl and cache sites, Internet Archive ( clearnet:http://archive.org/web ) stores publicly available content and so on. And NSA - it's basically best to assume that all your traffic is recorded.
In short, have a mindset that whatever you do in the internet will be recorded for eternity. So, always take a moment before hitting a "Post", "Register" or whatever button: think about what information are you sharing, how it can it connected to you and what consequences may it have. Not only today, but maybe after 20 years.
So, those are my personal suggestions. Another advice: never trust one source for information regarding security (for example my recommendations). Always read advice of at least several people and make some research yourself.
Feel free to ask if you have any issues or whatever. It's always better to ask, than possibly make a serious mistake regarding your personal security!
Stay safe,
~In Pain
Це звичайно ж мінамальний мінім того що треба знати, але і він як бачити не маленький, ТОМУ СТО РАЗ ПОДУМАЙТЕ ПЕРЕД ТИМ: ЯК ЛІЗТИ У ПАВУТИНУ ДО ПАВУКІВ БУДУЧИ МУХОЮ.
